
- admin
- April 17, 2025
- 1 Comment
AI-Driven Cyber Threats & Business Protection Strategies
AI-Powered Phishing Attacks
How it works: Attackers use generative AI (e.g., ChatGPT, deepfake tools) to craft highly convincing and personalized phishing emails, voice messages, or videos.
Threat level: High
Phishing Illustration
Automated Vulnerability Discovery
How it works: AI scans codebases and systems for exploitable vulnerabilities faster than traditional methods.
Threat level: Medium to High
Vulnerability Scan Illustration
AI-Driven Malware
How it works: Malware that adapts its behavior in real-time to avoid detection by traditional antivirus and EDR tools.
Threat level: High
Malware Illustration
Deepfake and Synthetic Identity Fraud
How it works: AI-generated videos or audio clips can impersonate company executives, leading to fraud, social engineering, or reputational damage.
Threat level: Medium to High
Deepfake Fraud Illustration
Data Poisoning & Adversarial Attacks
How it works: Attackers manipulate training data used in AI models to skew outcomes or insert backdoors.
Threat level: High
Data Poisoning Illustration
AI for Lateral Movement & Privilege Escalation
How it works: AI models predict optimal attack paths in a network after initial access, making lateral movement faster and stealthier.
Threat level: Medium to High
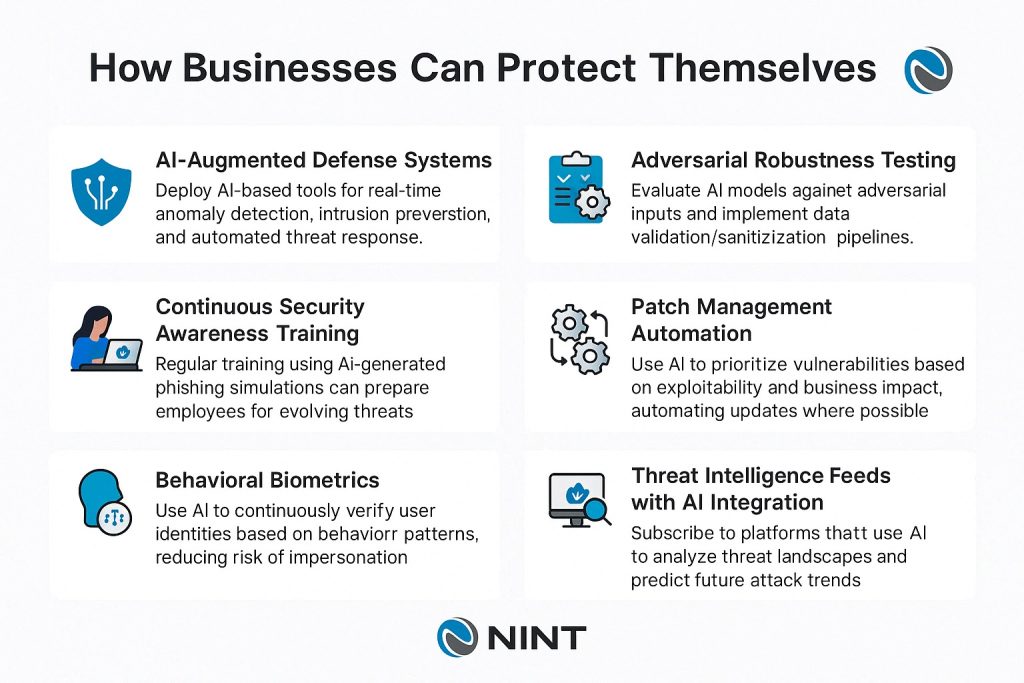
How Businesses Can Protect Themselves
AI-Augmented Defense Systems
Deploy AI-based tools for real-time anomaly detection, intrusion prevention, and automated threat response.
Continuous Security Awareness Training
Regular training using AI-generated phishing simulations to prepare employees for evolving threats.
Zero Trust Architecture
Limit lateral movement with microsegmentation, least privilege access, and strict authentication controls.
Behavioral Biometrics
Use AI to continuously verify user identities based on behavior patterns, reducing risk of impersonation.
Adversarial Robustness Testing
Evaluate AI models against adversarial inputs and implement data validation/sanitization pipelines.
Patch Management Automation
Use AI to prioritize vulnerabilities based on exploitability and business impact, automating updates where possible.
Threat Intelligence Feeds with AI Integration
Subscribe to platforms that use AI to analyze threat landscapes and predict future attack trends.
Deepfake Detection Tools
Implement specialized tools to detect manipulated media and synthetic voices.
1 Comment
Leave a Reply Cancel reply
You must be logged in to post a comment.
Categories
Tags
#tofseemalware
Blockchain
Cyber Attack
Cyber Awareness
Cybercrime
Cyber Security
Cyber Security Framework
DataPrivacy
EncryptedTraffic
ethicalhacking
Global News
Hacking & Mitigation
Information Security
kalilinux
learnkalilinux
NetworkSecurity
NextIsNowTechnologies
NINTCyberSecurity
paymentwallet
RemoteWorkSecurity
SecureConnection
Secured HTTPS Model
VPNExplained
ZeroTrustSecurity
good